Mobile IP and Transport Layer
Mobile IP?
The Mobile IP allows mobile device users to move from one network to another while maintaining the same permanent IP address.
The concept and role of Mobile IP are very important in the field of mobile computing technology.
The mobile IP makes the communication flawless and ensures that the communication will occur without the user's sessions or connections being dropped.
Mobile IP is based on IP, so it is scalable for the Internet. Any media that supports IP can also support Mobile IP.
Introduction to Mobile IP
Technology
In IP networks, when a device is within its home
network, the routing is based on the static IP addresses. The device within a
network is connected through normal IP routing by the IP address assigned on
the network. It is the same as how a postal letter is delivered to the fixed
address on the envelope. The problem occurs when a device goes away from its
home network and is no longer reachable using normal IP routing. In this
condition, the active sessions of the device are terminated. The idea of Mobile
IP was introduced to resolve this issue. It facilitates users to keep the same
IP address while going to a different network or a different wireless operator
without being communication disrupted or without sessions or connections being
dropped.
The mobility function of the Mobile IP is performed
on the network layer rather than the physical layer.
The architecture of Mobile IP
Technology
The components of the Mobile IP and the
relationship among them are specified in the following image:
This is the architecture of Mobile IP technology.
It consists of the following components:
- Mobile Node (MN)
- Home Agent (HA)
- Foreign Agent (FA)
- Home Network (HN)
- Foreign Network (FN)
- Corresponding Node (CN)
- Care of Address (COA)
Mobile Node
The Mobile Node is a device or a user or a router
that can frequently change their network positions without changing its
original IP address. Examples of mobile nodes are cell phone, personal digital
assistant (PDA), laptop, etc. whose software enables network roaming
capabilities.
Home Agent
The Home Agent is a router on the home network. It
serves as the anchor point for communication with the Mobile Node.
Foreign Agent
The Foreign Agent is a router that provides several
services such as tunneling data-grams whenever a mobile node visits a foreign
network. It is responsible for delivering packets from the Home Agent to the
Mobile Node.
Home Network
The home network is the base station network to
which the mobile node originally belongs to.
Foreign Network
Any network other than the home network or the
networks on which mobile nodes have a registered IP is called a foreign
network.
Corresponding Node
The partner nodes which are used for communication
with mobile nodes are called corresponding nodes.
Care of Address
The Care of Address or COA is used to define the
mobile node's current position or user. It is used to deliver data packets
through the process of tunneling.
Working of Mobile IP
The working of Mobile IP can be described in 3 phases:
Agent Discovery
In the Agent Discovery phase, the mobile nodes
discover their Foreign and Home Agents. The Home Agent and Foreign Agent
advertise their services on the network using the ICMP Router Discovery
Protocol (IRDP).
Registration
The registration phase is responsible for informing
the current location of the home agent and foreign agent for the correct
forwarding of packets.
Tunneling
This phase is used to establish a virtual
connection as a pipe for moving the data packets between a tunnel entry and a
tunnel endpoint.
Applications of Mobile IP
The mobile IP technology is used in many
applications where the sudden changes in network connectivity and IP address
can cause problems. It was designed to support seamless and continuous Internet
connectivity.
It is used in many wired and wireless environments
where users have to carry their mobile devices across multiple LAN subnets.
Although Mobile IP is not required within cellular
systems such as 3G, it is often used in 3G systems to provide seamless IP
mobility between different packet data serving node (PDSN) domains
IP packet delivery :
Mobile node (MN):
1. A mobile node is an end-system or router that can change its
point of attachment
to the internet using mobile IP.
2. The MN keeps its IP address and can continuously communicate
with any other
system in the internet as long
as link-layer connectivity is given.
3. Mobile nodes are not necessarily
small devices such as laptops with antennas or
mobile phones; a router onboard
an aircraft can be a powerful mobile node.
Correspondent node (CN):
At least one partner is needed
for communication. In the following the CN
represents this partner for the
MN. The CN can be a fixed or mobile node.
Mobile node (MN):
1. A mobile node is an end-system or router that can change its
point of attachment
to the internet using mobile IP.
2. The MN keeps its IP address and can continuously communicate
with any other
system in the internet as long
as link-layer connectivity is given.
3. Mobile nodes are not necessarily
small devices such as laptops with antennas or
mobile phones; a router onboard
an aircraft can be a powerful mobile node.
Correspondent node (CN):
At least one partner is needed
for communication. In the following the CN
represents this partner for the
MN. The CN can be a fixed or mobile node.
1. A correspondent node
CN wants to send an IP packet to the MN.
2. One
of the requirements of mobile IP was to
support hiding the mobility of
the MN.
3. CN
does not need to know
anything about the MN9s current
location and sends the packet as usual to the IP address of MN (step
1). This means that CN sends an IP
packet with MN as a destination address and CN as a source address.
The internet, not having
information on the
current location of MN, routes the packet to the router responsible
for the home network of MN. This is done using the standard routing mechanisms
of the internet
4. The HA now intercepts
the packet, knowing that MN is currently not in its home network.
5. The packet
is not forwarded
into the subnet
as usual, but
encapsulated and tunnelled to the
COA.
6. A new
header is put
in front of
the old IP
header showing the
COA as new destination and HA as source of the
encapsulated packet (step 2).
7. The foreign
agent now decapsulates
the packet, i.e.,
removes the additional header, and
forwards the original
packet with CN
as source and
MN as destination to the MN (step
3).
8. Again,
for the MN mobility is not visible. It
receives the packet
with the same sender and receiver address as it would
have done in the home network.
9. The MN sends the
packet as usual with its own fixed IP address as source and CN9s address as
destination (step 4).
10. The router with the
FA acts as default router and forwards the packet in the same way as it would
do for any other node in the foreign network.
As long as CN is a fixed node the remainder is in the fixed internet as
usual. If CN were also a mobile node
residing in a foreign network, the same mechanisms as described in steps 1
through 3 would apply now in the other direction.
Agent Discovery :
Here foreign agents and
home agents advertise their presence periodically using special agent
advertisement messages. ➢ These advertisement
messages can be seen as a beacon broadcast into the subnet. Routers in the
fixed network implementing this mechanisms also advertise their routing service
periodically to the attached links. The
agent advertisement packet according to RFC 1256 with the extension for
mobility is shown in Figure.
The upper part represents the ICMP packet while the lower part is the extension needed for mobility.
1. The TTL
field of the
IP packet is
set to 1 for all
advertisements to avoid forwarding them.
2. The IP
destination address according
to standard router
advertisements can be either
set to 224.0.0.1,
which is the
multicast address for
all systems on
a link (Deering, 1989), or to the
broadcast address 255.255.255.255.
3. The fields in the ICMP
part are defined as follows. The type is set to 9, the code can be 0, if the
agent also routes traffic from non-mobile nodes, or 16, if it does not route
anything other than mobile traffic.
4. Foreign agents are at
least required to forward packets from the mobile node.
5. The number
of addresses advertised
with this packet
is in #addresses
while the addresses themselves
follow as shown.
6. Lifetime denotes the
length of time this advertisement is valid.
7. Preference levels
for each address
help a node
to choose the
router that is
the most eager one to get a new
node.
8. The difference
compared with standard
ICMP advertisements is
what happens after the router
addresses.
9. This extension
for mobility has
the following fields
defined: type is
set to 16, length depends on the number of COAs
provided with the message and equals 6 + 4*(number of addresses).
10. An agent shows the
total number of advertisements sent since initialization in the sequence
number.
11. By the
registration lifetime, the
agent can specify
the maximum lifetime
in seconds a node can request during registration.
12. The following bits
specify the characteristics of an agent in detail.
◼
The R bit (registration) shows, if a registration with this agent is required
even when using a colocated COA at the MN.
◼
If the agent is currently too busy to accept new registrations it can set the B
bit.
◼
The following two
bits denote if
the agent offers
services as a home
agent (H) or foreign agent (F)
on the link where the advertisement has been sent.
◼
Bits M and G specify the method of encapsulation used for the tunnel.
◼
While IP-in-IP encapsulation
is the mandatory
standard, M can
specify minimal encapsulation and G generic routing encapsulation.
◼
In the first version of mobile IP (RFC 2002) the V bit specified the use of
header compression according
to RFC 1144
(Jacobson,1990). Now the field r
at the same bit position is set to zero and must be ignored.
◼
The new
field T indicates that
reverse tunneling is
supported by the FA.
◼
The following fields contain the COAs advertised.
◼
A foreign agent setting the F bit must advertise at least one COA.
A mobile node in a subnet
can now receive agent advertisements from either its home agent or a foreign
agent. This is one way for the MN to
discover its location.
Agent solicitation :
1. If no agent advertisements are present or
the inter-arrival time is too high, and an MN has not received a COA by other
means, e.g., DHCP, the mobile node must send agent solicitations.
2. Care must
be taken to
ensure that these
solicitation messages do
not flood the network,
but basically an MN can
search for an
FA endlessly sending
out solicitation messages.
3. Typically, a mobile
node can send out three solicitations, one per second, as soon as it enters a
new network.
4. It should
be noted that
in highly dynamic
wireless networks with
moving MNs and probably
with applications requiring
continuous packet streams
even one second intervals between
solicitation messages might be too long.
5. Before an
MN even gets
a new address
many packets will
be lost without additional mechanisms.
6. If a node does not
receive an answer to its solicitations it must decrease the rate of
solicitations exponentially to
avoid flooding the
network until it
reaches a maximum interval
between solicitations (typically one minute).
7. Discovering a new
agent can be done anytime, not just if the MN is not connected to one. 8.
Consider the case that an
MN is looking
for a better
connection while still sending via the old path.
9. This is the case while
moving through several cells of different wireless networks. After these
steps of advertisements or
solicitations the MN can now
receive a COA, either one for an
FA or a co-located COA.
10. The MN
knows its location
(home network or
foreign network) and
the capabilities of the agent (if needed).
Tunnelling and Encapsulation:
A tunnel establishes a
virtual pipe for data packets between a tunnel entry and a tunnel
endpoint. Packets entering a tunnel are
forwarded inside the tunnel and leave the tunnel unchanged. Tunneling, i.e., sending a packet through a
tunnel, is achieved by using encapsulation.
Encapsulation is the mechanism of taking a packet consisting of packet
header and data and putting it into the data part of a new packet. The reverse operation, taking a packet out of
the data part of another packet, is called decapsulation.
Encapsulation and
decapsulation are the operations typically performed when apacket is
transferred from a higher protocol layer to a lower layer or from a lower to a
higher layer respectively.
Here these
functions are used
within the same
layer. This mechanism
is shown in Figure 4 and describes exactly what the HA at the tunnel
entry does. Fig 4 : IP
Encapsulation The HA takes the
original packet with the MN as destination, puts it into the data part of a new packet and sets the new IP
header in such a way that the packet is routed to the COA.
The new header is also
called the outer header for obvious reasons.
Additionally, there is
an inner header which
can be identical
to the original header as
this is the
case for IP-in-IP
encapsulation, or the
inner header can be
computed during encapsulation.
Route Optimization in Mobile IP:
The route optimization
adds a conceptual data structure, the binding cache, to the correspondent node.
The binding cache contains 2. bindings for mobile node’s home address and its
current care-of-address. Every time the home agent receives a IP datagram that
is destined to a mobile node currently away from the home network, it sends a
binding update to the correspondent node to update the information in the
correspondent node’s binding cache. After this the correspondent node can
directly tunnel packets to the mobile node.
Process of Mobile IP The mobile IP process has following three main phases, which are:
1. Agent Discovery During
the agent discovery phase the HA and FA advertise their services on the network
by using the ICMP router discovery protocol (IROP). Mobile IP defines two
methods: agent advertisement and agent solicitation which are in fact router
discovery methods plus extensions. o Agent advertisement: For the first method,
FA and HA advertise their presence periodically using special agent
advertisement messages. These messages advertisement can be seen as a beacon
broadcast into the subnet. For this advertisement internet control message
protocol (ICMP) messages according to RFC 1256, are used with some mobility
extensions. o Agent solicitation: If no agent advertisements are present or the
inter arrival time is too high, and an MN has not received a COA, the mobile
node must send agent solicitations. These solicitations are again bases on RFC
1256 for router solicitations.
2. Registration The main
purpose of the registration is to inform the home agent of the current location
for correct forwarding of packets.
Registration can be done in two ways depending on the location of the COA. o If the COA is at the FA, the MN sends its registration request containing the COA to the FA which is forwarding the request to the HA. The HA now set up a mobility binding containing the mobile node's home IP address and the current COA. Additionally, the mobility biding contains the lifetime of the registration which is negotiated during the registration process. Registration expires automatically after the lifetime and is deleted; so a mobile node should register before expiration. After setting up the mobility binding, the HA send a reply message back to the FA which forwards it to the MN. o If the COA is co-located, registration can be very simpler. The mobile node may send the request directly to the HA and vice versa. This by the way is also the registration procedure for MNs returning to their home network.
3. Tunneling A tunnel is
used to establish a virtual pipe for data packets between a tunnel entry and a
tunnel endpoint. Packets which are entering in a tunnel are forwarded inside
the tunnel and leave the tunnel unchanged. Tunneling, i.e., sending a packet
through a tunnel is achieved with the help of encapsulation. Tunneling is also
known as "port forwarding" is the transmission and data intended for
use only within a private, usually corporate network through a public network.
Transport Layer
TRADITIONAL
TCP Mechanisms that influence the efficiency of TCP in a mobile environment
•
Congestion control
•
Slow start
•
Fast retransmit/fast recovery
•
Implications on mobility
Congestion control
•
TCP has been designed for fixed networks with fixed end-systems
•
Hardware and software are mature enough to ensure reliability of data
•
The probable reason for a packet loss in a fixed network is a temporary overload
some point in the transmission path, i.e., a state of congestion at a node
•
The packet buffers of a router are filled and the router cannot forward the
packets fast enough • The only thing a router can do in this situation is to
drop packets
• The
sender notices the missing acknowledgement for the lost packet and assumes a
packet loss due to congestion
•
Retransmitting the missing packet and continuing at full sending rate would now
be unwise, as this might only increase the congestion. Slow start
•
The behavior TCP shows after the detection of congestion is called slow start
•
The sender always calculates a congestion window for a receiver.
•
The start size of the congestion window is one segment (TCP packet).
•
This scheme doubles the congestion window every time the acknowledgements come
back, which takes one round trip time (RTT) like 1, 2, 4, 8 etc.
•
This is called the exponential growth of the congestion window in the slow
start mechanism. • The exponential growth stops at the congestion threshold.
Slow start
•
The behavior TCP shows after the detection of congestion is called slow start
•
The sender always calculates a congestion window for a receiver.
•
The start size of the congestion window is one segment (TCP packet).
• This scheme doubles the congestion window
every time the acknowledgements come back, which takes one round trip time
(RTT) like 1, 2, 4, 8 etc.
•
This is called the exponential growth of the congestion window in the slow
start mechanism. • The exponential growth stops at the congestion threshold.
As soon as the congestion
window reaches the congestion threshold, further increase of the transmission
rate is only linear by adding 1 to the congestion window each time the
acknowledgements come back
• Linear increase
continues until a time-out at the sender occurs due to a missing
acknowledgement, or until the sender detects a gap in transmitted data o the
sender sets the congestion threshold to half of the current congestion window o
The congestion window itself is set to one segment Fast retransmit/fast
recovery Fast Retransmit
• a receiver sends
acknowledgements only if it receives any packets from the sender. • Receiving
acknowledgements from a receiver also shows that the receiver continuously
receives something from the sender.
• The gap in the packet
stream is not due to severe congestion, but a simple packet loss due to a
transmission error.
• The sender can now
retransmit the missing packet(s) before the timer expires. • This behavior is
called fast retransmit Fast Recovery
• The receipt of
acknowledgements shows that there is no congestion to justify a slow start.
• The sender can continue
with the current congestion window.
• The sender performs a
fast recovery from the packet loss
• This mechanism can
improve the efficiency of TCP dramatically Implications on mobility
• TCP concludes a
congestion situation from a missing acknowledgement o typically wrong in
wireless networks, here we often have packet loss due to transmission errors o
mobility itself can cause packet loss, if e.g. a mobile node roams from one
access point (e.g. foreign agent in Mobile IP) to another while there are still
packets in transit to the wrong access point and forwarding is not possible •
The performance of an unchanged TCP degrades severely o TCP cannot be changed
fundamentally due to the large base of installation in the fixed network,
▪ TCP for mobility has to remain compatible o
the basic TCP mechanisms keep the whole Internet together CLASSICAL TCP
IMPROVEMENTS
• Indirect TCP (I-TCP)
• Snooping TCP • Mobile
TCP
• Fast retransmit/fast
recovery
• Transmission/time-out
freezing
• Selective
retransmission
• Transaction-oriented
TCP
Indirect
TCP (I-TCP)
I-TCP segments a TCP connection into a o fixed part - Standard TCP is used o wireless part - optimized TCP protocol
• splitting of the TCP
connection at, e.g., the foreign agent into 2 TCP connections, no real
end-to-end connection any longer
• hosts in the fixed part
of the net do not notice the characteristics of the wireless part
Advantages
• no changes in the fixed
network necessary, no changes for the hosts (TCP protocol) necessary, all
current optimizations to TCP still work
• transmission errors on
the wireless link do not propagate into the fixed network
• simple to control,
mobile TCP is used only for one hop between, e.g., a foreign agent and mobile
host
• therefore, a very fast
retransmission of packets is possible, the short delay on the mobile hop is
known
Disadvantages
• loss of end-to-end
semantics, an acknowledgement to a sender does now not any longer mean that a
receiver really got a packet, foreign agents might crash
• higher latency possible
due to buffering of data within the foreign agent and forwarding to a new FA
Snooping
TCP
• the foreign agent
buffers all packets with destination mobile host and additionally ‘snoops’ the
packet flow in both directions to recognize acknowledgements
• buffering enable the FA
to perform a local retransmission in case of packet loss on the wireless link
• Transparent extension
of TCP within the foreign agent
• buffering of packets
sent to the mobile host
• lost packets on the
wireless link (both directions!) will be retransmitted immediately by the
mobile host or foreign agent, respectively (so called “local” retransmission)
• the foreign agent
therefore “snoops” the packet flow and recognizes acknowledgements in both
directions, it also filters ACKs
• changes of TCP only
within the foreign agent
• Data transfer to the mobile host o FA buffers data until it receives ACK of the MH, FA detects packet loss via duplicated ACKs or time-out o fast retransmission possible, transparent for the fixed network
• Data transfer from the
mobile host o FA detects packet loss on the wireless link via sequence numbers,
▪ FA answers directly
with a NACK to the MH o MH can now retransmit data with only a very short delay
• Integration of the MAC
layer o MAC layer often has similar mechanisms to those of TCP o thus, the MAC
layer can already detect duplicated packets due to retransmissions and discard
them
• Problems o snooping TCP
does not isolate the wireless link as good as I-TCP o snooping might be useless
depending on encryption schemes
Advantages
• The end-to-end TCP
semantic is preserved
• The correspondent host
does not need to be changed; most of the enhancements are in the foreign agent
• It does not need a
handover of state as soon as the mobile host moves to another foreign agent. •
It does not matter if the next foreign agent uses the enhancement or not
Disadvantages
• Snooping TCP does not
isolate the behavior of the wireless link as well as ITCP
• Using negative
acknowledgements between the foreign agent and the mobile host assumes
additional mechanisms on the mobile host.
• All efforts for
snooping and buffering data may be useless if certain encryption schemes are
applied end-to- end between the correspondent host and mobile host
Mobile TCP
• Special handling of
lengthy and/or frequent disconnections
• M-TCP splits as I-TCP
does
o unmodified TCP fixed
network to supervisory host (SH)
o optimized TCP SH to MH
• Supervisory host o no
caching, no retransmission o monitors all packets, if disconnection detected ▪
set sender window size to 0
▪ sender automatically
goes into persistent mode
o old or new SH reopen
the window
• Advantages
o maintains semantics, supports
disconnection, no buffer forwarding
• Disadvantages
o loss on wireless link
propagated into fixed network o adapted TCP on wireless link
Fast
retransmit / fast recovery
• Change of foreign agent
often results in packet loss
o TCP reacts with slow-start
although there is no congestion
• Forced fast retransmit
o as soon as the mobile host has registered with a new foreign agent, the MH
sends duplicated acknowledgements on purpose
o this forces the fast
retransmit mode at the communication partners o additionally, the TCP on the MH
is forced to continue sending with the actual window size and not to go into
slow-start after registration
• Advantage
o simple changes result
in significant higher performance
• Disadvantage
o further mix of IP and
TCP, no transparent approach Transmission / time-out freezing
• Mobile hosts can be
disconnected for a longer time o no packet exchange possible, e.g., in a
tunnel, disconnection due to overloaded cells or mux. with higher priority
traffic
o TCP disconnects after
time-out completely
TCP freezing o MAC layer
is often able to detect interruption in advance
o MAC can inform TCP
layer of upcoming loss of connection o TCP stops sending, but does now not
assume a congested link
o MAC layer signals again
if reconnected
• Advantage
o scheme is independent
of data
• Disadvantage
o TCP on mobile host has
to be changed, mechanism depends on MAC layer
Selective
retransmission
• TCP acknowledgements
are often cumulative o ACK n acknowledges correct and in-sequence receipt of
packets up to n
o if single packets are
missing quite often a whole packet sequence beginning at the gap has to be
retransmitted (go-back-n), thus wasting bandwidth
• Selective
retransmission as one solution
o RFC2018 allows for
acknowledgements of single packets, not only acknowledgements of in-sequence
packet streams without gaps
o sender can now
retransmit only the missing packets
• Advantage
o much higher efficiency
• Disadvantage
o more complex software
in a receiver, more buffer needed at the receiver
Transaction-oriented
TCP
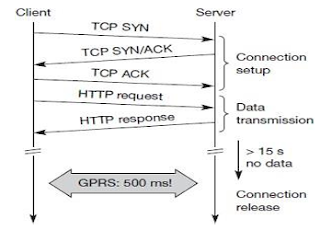
• TCP phases o setup,
data transmission, connection release o using 3-way-handshake needs 3 packets
for setup and release, respectively o thus, even short messages need a minimum
of 7 packets!
• Transaction oriented
TCP o RFC1644, T-TCP, describes a TCP version to avoid this overhead
o connection setup, data
transfer and connection release can be combined o thus, only 2 or 3 packets are
needed
• Advantage : efficiency
• Disadvantage o requires
changed TCP o mobility not longer transparent.










Comments
Post a Comment